DrayTek UK Users' Community Forum
Help, Advice and Solutions from DrayTek Users
Draytek 2955 - L2TP vulnerability causing reboots?
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
09 Nov 2018 17:44 #93341
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Just been told by Draytek that the 2955 supports neither IKEV2 nor XAUTH...
So for Android, or Windows, it appears that the only VPN options are PPTP or L2TP/IPSEC but the latter keeps rebooting it (very random timing; probably hackers manage to crash it).
Maybe there is an IKEV1 windows VPN client?
The Greenbow VPN client does IKEV1 but I cannot get it to work. Syslog shows it getting quite far though but no connection is established.
So for Android, or Windows, it appears that the only VPN options are PPTP or L2TP/IPSEC but the latter keeps rebooting it (very random timing; probably hackers manage to crash it).
Maybe there is an IKEV1 windows VPN client?
The Greenbow VPN client does IKEV1 but I cannot get it to work. Syslog shows it getting quite far though but no connection is established.
Please Log in or Create an account to join the conversation.
- hornbyp
- Offline
- Big Contributor
-

Less
More
- Posts: 1323
- Thank you received: 0
09 Nov 2018 23:07 #93343
by hornbyp
That's the conclusion I've come to, after playing with the2955 emulator:
http://eu.draytek.com:12955/
Don't discount SmartVPN/SSL for your phone - that's what I use for a quick login .. where throughput doesn't matter. It very rarely malfunctions (and even makes it through the Great FIrewall of China!). It's usable on a PC, I guess you're more likely to notice the lack of ooompph (if you're trying to watch ITV Player from a Florida villa, for example!)
I had a quick play with it, but got nowhere ...
...however, see:
https://www.draytek.co.uk/support/guides/kb-dialinvpn-greenbow#aggressive-mode
. It's possible that I didn't actually follow this guide, though I've definitely seen it before.
Note: there's a paragraph on there that sums up the whole Main Mode/Aggressive Mode thing :-
I might have another play with it, because I cannot get "Aggressive Mode" for Remote Dial-in users to work at all on either the2830 and the 2860 .
Replied by hornbyp on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Just been told by Draytek that the 2955 supports neither IKEV2 nor XAUTH...peter-h wrote:
That's the conclusion I've come to, after playing with the
So for Android, or Windows, it appears that the only VPN options are PPTP or L2TP/IPSEC...
Don't discount SmartVPN/SSL for your phone - that's what I use for a quick login .. where throughput doesn't matter. It very rarely malfunctions (and even makes it through the Great FIrewall of China!). It's usable on a PC, I guess you're more likely to notice the lack of ooompph (if you're trying to watch ITV Player from a Florida villa, for example!)
The Greenbow VPN client does IKEV1 but I cannot get it to work. Syslog shows it getting quite far though but no connection is established.
I had a quick play with it, but got nowhere ...
...however, see:
Note: there's a paragraph on there that sums up the whole Main Mode/Aggressive Mode thing :-
The GreenBow client is able to use either Main Mode or Aggressive Mode to connect:They wrote:
Main Mode - This uses the router's global pre-shared key for dial-in users for all dial-in users connecting with IPsec.
Aggressive Mode - This uses a pre-shared key set per user account and the user identifies with its Peer ID setting. This is regarded as being slightly cryptographically less secure than main mode but does make it possible to manage multiple users .
I might have another play with it, because I cannot get "Aggressive Mode" for Remote Dial-in users to work at all on either the
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
10 Nov 2018 16:27 #93345
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
I need the st00pid login for that draytek article, and my draytek forum login doesn't work for it.
At €58 I would have paid for that VPN app but not if it is a hassle. It is really strange in its user interface. For example the only opportunity to config the server IP is by using the wizard to create the VPN profile. After that, I could not find where this is located!
Anyway, all my "research" suggests that PPTP (with MPPE or CHAPv2) is as secure as cracking standard DES, which I know a bit about since I have written some DES implementations and the fastest attacks (short of being able to inject chosen plaintext, which is not possible in this case), UNLESS somebody can set up a man in the middle attack, which in my scenario (occassional VPN use when travelling i.e. from random locations) is highly unlikely, are computationally infeasible. Even standard DES would take years on a fast PC.
It doesn't matter how much googling one does on PPTP security, one finds the same regurtation of the same repeated texts... There seems to be no known attack on the server port alone, other than guessing the login credentials. Unless of course Draytek have a back door in there (I read years ago they implemented a back door with a password of "drayteker" - do a google on it) or have a weakness e.g. buffer overflows.
I am finding various hacking attempts at both routers, from these IPs
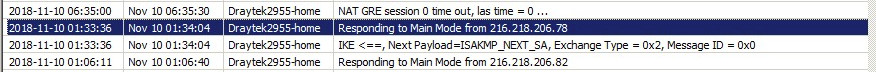
and googling them shows them as known for VPN attacks. I could reconfig L2TP and see if the router reboots coincide with these in the syslog but I won't bother because the connection is really obvious.
I wonder what is "Main mode"? It sounds like a hack into one of the VPN ports, which then passes to the code which tries to establish which of the VPN profiles it is meant for.
I could spend a few hundred on newer routers but with Draytek having gone into silent mode, there is no assurance they would be any better.
At €58 I would have paid for that VPN app but not if it is a hassle. It is really strange in its user interface. For example the only opportunity to config the server IP is by using the wizard to create the VPN profile. After that, I could not find where this is located!
Anyway, all my "research" suggests that PPTP (with MPPE or CHAPv2) is as secure as cracking standard DES, which I know a bit about since I have written some DES implementations and the fastest attacks (short of being able to inject chosen plaintext, which is not possible in this case), UNLESS somebody can set up a man in the middle attack, which in my scenario (occassional VPN use when travelling i.e. from random locations) is highly unlikely, are computationally infeasible. Even standard DES would take years on a fast PC.
It doesn't matter how much googling one does on PPTP security, one finds the same regurtation of the same repeated texts... There seems to be no known attack on the server port alone, other than guessing the login credentials. Unless of course Draytek have a back door in there (I read years ago they implemented a back door with a password of "drayteker" - do a google on it) or have a weakness e.g. buffer overflows.
I am finding various hacking attempts at both routers, from these IPs

and googling them shows them as known for VPN attacks. I could reconfig L2TP and see if the router reboots coincide with these in the syslog but I won't bother because the connection is really obvious.
I wonder what is "Main mode"? It sounds like a hack into one of the VPN ports, which then passes to the code which tries to establish which of the VPN profiles it is meant for.
I could spend a few hundred on newer routers but with Draytek having gone into silent mode, there is no assurance they would be any better.
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
10 Nov 2018 20:47 #93347
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
OK here goes another report 
AFTER doing the above discussed changes to the IPSEC stuff, I have managed to set up these VPNs
- winXP PPTP
- win10 PPTP
- android 5 PPTP Samsung T705
- android 6 PPTP Samsung S7
Obviously the above are not related to the IPSEC stuff and these do "just work" out of the box.
Now the interesting bit:
- winXP L2TP NO GO
- win10 L2TP works
- android 5 L2TP NO GO
- android 6 L2TP works
I can see syslog activity on the NO GO ones but don't understand it well enough to debug it. On winXP there are tons of config options, on win10 the defaults work. On android there are almost no config options. In all cases the L2TP VPN config asks for the PSK and then the login+pwd.
Previously, before I selected the Aggressive option in IPSEC, the winXP machine was fine with L2TP. But there could be any other problem too.
Another curious thing I found was that L2TP would not connect unless I had a username different from the PPTP one. I guess the router, upon the incoming VPN connection request, cannot tell which teleworker (or any) VPN profile to extract the credentials from. The site-site VPN doesn't have a username at all; just the shared key. So if you have multiple teleworker profiles, you probably need them to all have different usernames. Normally that would be the case because they would be different people, but in this case I had two profiles for myself; one with PPTP and one with L2TP/IPSEC.
I am done with this business now.
I have PPTP which works perfectly. Except that PPTP, using the GRE protocol (not TCP), doesn't run in some situations, notably some hotel wifi networks. I suspect it also doesn't run over some 3G/4G networks but it works over Vodafone UK contract (and AFAIK Voda PAYG is exactly the same as contract on network support). On mobile data, the data is tunneled over the GSM network all the way to the network provider's base and only there it goes into the internet, so your location should not affect whether a particular protocol works or not (which is why if you hit some website with your phone while you are roaming in Kathmandu, your IP on the web server will be showing "Vodafone London").
I also have L2TP working where I really need it, on the win10 laptop and on my phone. L2TP should work over any wifi network. I have found it will also tunnel via a port 443 Softether VPN I have on the laptop. (PPTP won't tunnel through that Softether VPN).
Now, with L2TP again enabled on the two sites, I will monitor syslog for any hacks which coincide with line drops (I get email and SMS notifications of line drops).
AFTER doing the above discussed changes to the IPSEC stuff, I have managed to set up these VPNs
- winXP PPTP
- win10 PPTP
- android 5 PPTP Samsung T705
- android 6 PPTP Samsung S7
Obviously the above are not related to the IPSEC stuff and these do "just work" out of the box.
Now the interesting bit:
- winXP L2TP NO GO
- win10 L2TP works
- android 5 L2TP NO GO
- android 6 L2TP works
I can see syslog activity on the NO GO ones but don't understand it well enough to debug it. On winXP there are tons of config options, on win10 the defaults work. On android there are almost no config options. In all cases the L2TP VPN config asks for the PSK and then the login+pwd.
Previously, before I selected the Aggressive option in IPSEC, the winXP machine was fine with L2TP. But there could be any other problem too.
Another curious thing I found was that L2TP would not connect unless I had a username different from the PPTP one. I guess the router, upon the incoming VPN connection request, cannot tell which teleworker (or any) VPN profile to extract the credentials from. The site-site VPN doesn't have a username at all; just the shared key. So if you have multiple teleworker profiles, you probably need them to all have different usernames. Normally that would be the case because they would be different people, but in this case I had two profiles for myself; one with PPTP and one with L2TP/IPSEC.
I am done with this business now.
I have PPTP which works perfectly. Except that PPTP, using the GRE protocol (not TCP), doesn't run in some situations, notably some hotel wifi networks. I suspect it also doesn't run over some 3G/4G networks but it works over Vodafone UK contract (and AFAIK Voda PAYG is exactly the same as contract on network support). On mobile data, the data is tunneled over the GSM network all the way to the network provider's base and only there it goes into the internet, so your location should not affect whether a particular protocol works or not (which is why if you hit some website with your phone while you are roaming in Kathmandu, your IP on the web server will be showing "Vodafone London").
I also have L2TP working where I really need it, on the win10 laptop and on my phone. L2TP should work over any wifi network. I have found it will also tunnel via a port 443 Softether VPN I have on the laptop. (PPTP won't tunnel through that Softether VPN).
Now, with L2TP again enabled on the two sites, I will monitor syslog for any hacks which coincide with line drops (I get email and SMS notifications of line drops).
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
14 Nov 2018 22:03 #93366
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Draytek tell me that the VPN ports bypass the firewall, so if somebody is trying to hack the VPN, always from e.g. the same IP, you can't block him.
Only once the VPN is open can the firewall be used (presumably using the "LAN" rather than "WAN" option - I don't understand how the same firewall can work in two places) but then the hacker has obviously got the login credentials...
Only once the VPN is open can the firewall be used (presumably using the "LAN" rather than "WAN" option - I don't understand how the same firewall can work in two places) but then the hacker has obviously got the login credentials...
Please Log in or Create an account to join the conversation.
- hornbyp
- Offline
- Big Contributor
-

Less
More
- Posts: 1323
- Thank you received: 0
15 Nov 2018 00:15 #93367
by hornbyp
Replied by hornbyp on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
The answer, apparently, is to add the offender to the DoS Flood Table 'Blacklist'
According to:
https://www.draytek.com/faq/faq-security/security.firewall/how-to-block-an-unknown-ip-which-keeps-dialing-ipsec-vpn-to-vigor-router#When-using-DrayOS-router-as-VPN-server
This is an interesting bit of lateral thinking, but unfortunately, the option seems to be missing from the 2955
emulator
) 
(Amusingly, I added a firewall rule to my 2830
On another topic, I had another go with the Greenbow client
According to:
This is an interesting bit of lateral thinking, but unfortunately, the option seems to be missing from the 2955
(Amusingly, I added a firewall rule to my 2830
On another topic, I had another go with the Greenbow client
Please Log in or Create an account to join the conversation.
Moderators: Chris, Sami
Copyright © 2024 DrayTek


