DrayTek UK Users' Community Forum
Help, Advice and Solutions from DrayTek Users
Draytek 2955 - L2TP vulnerability causing reboots?
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
08 Nov 2018 21:38 #93329
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Thank you for the time you have put in 
Unfortunately the 2955 config screens look nothing like the 3900's.
This is what I see under the Teleworker setup:
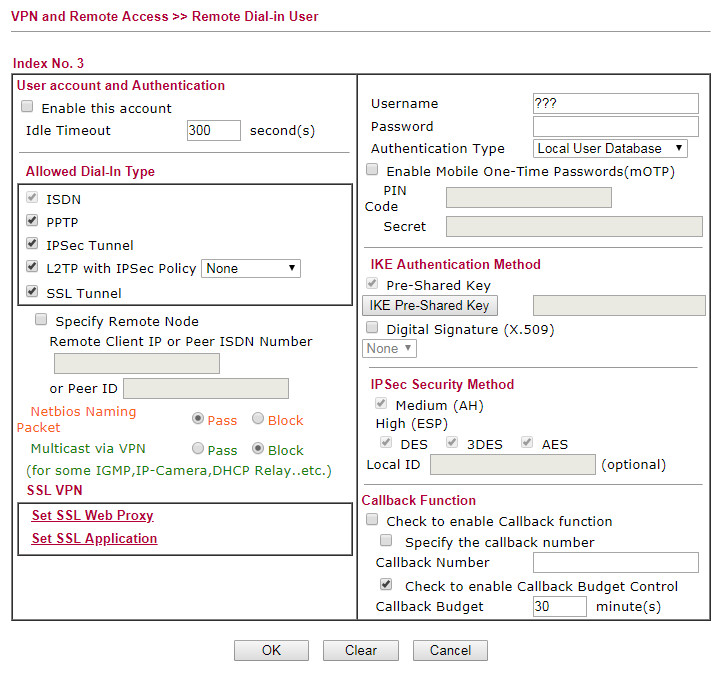
I would uncheck all the VPN types except IPSEC Tunnel.
And this is the PSK config screen, where what looks like the only password used for the site-site IPSEC VPN is set up:
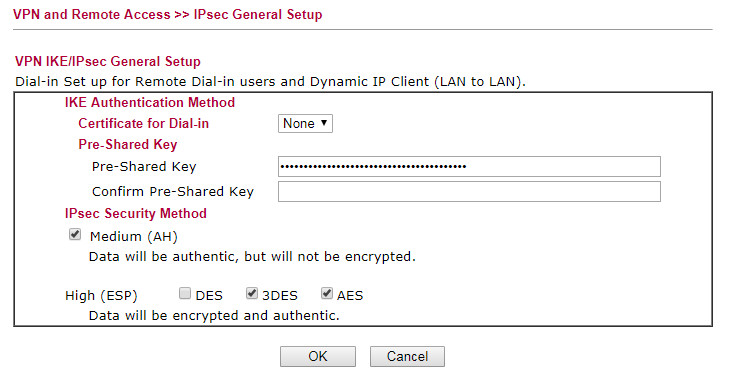
Unfortunately the 2955 config screens look nothing like the 3900's.
This is what I see under the Teleworker setup:

I would uncheck all the VPN types except IPSEC Tunnel.
And this is the PSK config screen, where what looks like the only password used for the site-site IPSEC VPN is set up:

Please Log in or Create an account to join the conversation.
- hornbyp
- Offline
- Big Contributor
-

Less
More
- Posts: 1323
- Thank you received: 0
08 Nov 2018 23:38 #93331
by hornbyp
I know - it makes life interesting
That sounds about right, but I think you should untick [ ] Medium (AH
3DES has surely had its day and in my experiments, when (AH)NO
:shock:
That
For LAN to LAN (Site to Site)
Initiating End

Target router

Replied by hornbyp on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Unfortunately the 2955 config screens look nothing like the 3900's.peter-h wrote:
I know - it makes life interesting
This is what I see under the Teleworker setup:
I would uncheck all the VPN types except IPSEC Tunnel.
And this is the PSK config screen, where what looks like the only password used for the site-site IPSEC VPN is set up:
That sounds about right, but I think you should untick [ ] Medium (AH
3DES has surely had its day and in my experiments, when (AH)
That
For LAN to LAN (Site to Site)


Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
09 Nov 2018 10:07 #93333
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
I will try this tonight, hornby, but do you think the 2955 works at all with IKEv2 which is the only option on win10?
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
09 Nov 2018 11:22 #93334
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
This is what I currently have in the lan-lan profile
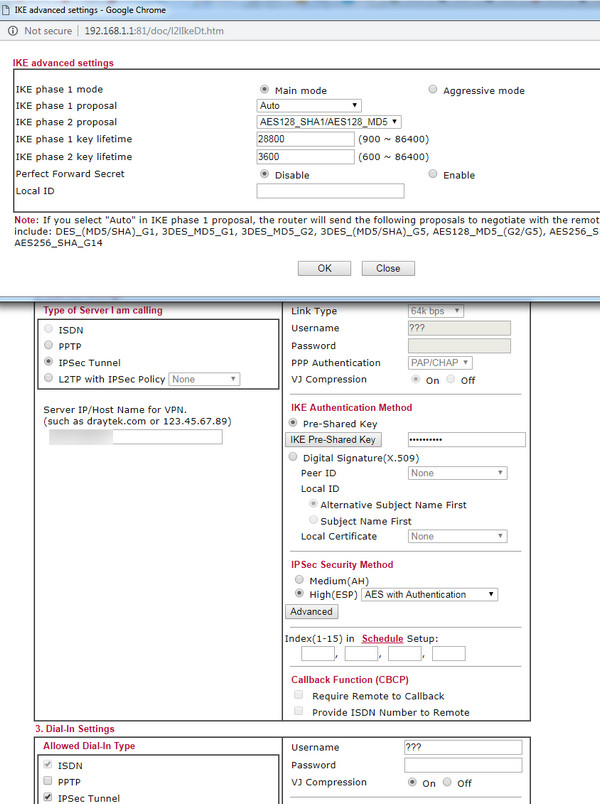
The problem is that I don't want to break the lan-lan profile, which is working fine.
Currently I am not using the Peer ID in the lan-lan profile, instead relying on the PSK wholly for security.

The problem is that I don't want to break the lan-lan profile, which is working fine.
Currently I am not using the Peer ID in the lan-lan profile, instead relying on the PSK wholly for security.
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
09 Nov 2018 13:14 #93336
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Well, I have modded the lan-lan profile as suggested, with the Peer ID configured, and Aggressive mode chosen.
It just breaks the lan-lan function. Clearly Draytek never tested the various options
So I am going back to PPTP. I've been doing some reading and PPTP (IF the client uses MPPE, known as MSCHAP in a win machine) has no real vulnerability except the MITM attack which is possible only if a session is running. So not suitable for a site-site VPN but fine for the occassional remote access. There is no magic with VPN's; all the VPN ports are readibly discoverable with a sniffer and *will* be hit 24/7 by the chinese etc. So you must have suitably un-guessable login credentials.
One downside of PPTP is that it no longer appears to work over Vodafone 4G, but on a windows machine I can open another VPN first and then run PPTP through that. It is only on android where only one VPN can be active.
This old appnote (without Mikey's articles almost nobody could have got Draytek routers to work, in those days
https://www.draytek.co.uk/archive/kb_vigor_vpncheck.html
has an interesting note:
"Do not use the same username for a dial-in (teleworker) user profile as for a LAN-to-LAN profile. The router is unable to tell which one you want when the call comes in and so will default to the Teleworker. A LAN-LAN connection can still be established but no routing will occur as the IP allocated will be for a single teleworker only."
which is probably relevant to a lot of problems. HOW does the server end know what sort of VPN client is calling in? I guess it could guess by applying some rules to what is arriving and guessing the authentication being requested, and then going through the various VPN profiles to see who has that form of security configured.
My lan-lan VPN has no "caller ID". The teleworker VPNs all do have one (the username / password fields) so the router can tell which teleworker is calling. So it must assume that an incoming call (if say all VPNs were of the same type) without an ID must be the lan-lan VPN. Bizzare!
Just found this:
https://www.draytek.com/en/faq/faq-vpn/vpn.others/why-the-vpn-connection-cannot-be-established/
"If VPN Profile on VPN server has Specify Remote VPN IP or Peer ID, Pre-Shared Key should be configured by clicking IKE Pre-Shared Key button in Dial-In Settings of VPN profiles."
That is REALLY interesting.
It just breaks the lan-lan function. Clearly Draytek never tested the various options
So I am going back to PPTP. I've been doing some reading and PPTP (IF the client uses MPPE, known as MSCHAP in a win machine) has no real vulnerability except the MITM attack which is possible only if a session is running. So not suitable for a site-site VPN but fine for the occassional remote access. There is no magic with VPN's; all the VPN ports are readibly discoverable with a sniffer and *will* be hit 24/7 by the chinese etc. So you must have suitably un-guessable login credentials.
One downside of PPTP is that it no longer appears to work over Vodafone 4G, but on a windows machine I can open another VPN first and then run PPTP through that. It is only on android where only one VPN can be active.
This old appnote (without Mikey's articles almost nobody could have got Draytek routers to work, in those days
has an interesting note:
"Do not use the same username for a dial-in (teleworker) user profile as for a LAN-to-LAN profile. The router is unable to tell which one you want when the call comes in and so will default to the Teleworker. A LAN-LAN connection can still be established but no routing will occur as the IP allocated will be for a single teleworker only."
which is probably relevant to a lot of problems. HOW does the server end know what sort of VPN client is calling in? I guess it could guess by applying some rules to what is arriving and guessing the authentication being requested, and then going through the various VPN profiles to see who has that form of security configured.
My lan-lan VPN has no "caller ID". The teleworker VPNs all do have one (the username / password fields) so the router can tell which teleworker is calling. So it must assume that an incoming call (if say all VPNs were of the same type) without an ID must be the lan-lan VPN. Bizzare!
Just found this:
"If VPN Profile on VPN server has Specify Remote VPN IP or Peer ID, Pre-Shared Key should be configured by clicking IKE Pre-Shared Key button in Dial-In Settings of VPN profiles."
That is REALLY interesting.
Please Log in or Create an account to join the conversation.
- peter-h
- Topic Author
- Offline
- Junior Member
-

Less
More
- Posts: 60
- Thank you received: 0
09 Nov 2018 15:50 #93339
by peter-h
Replied by peter-h on topic Re: Draytek 2955 - L2TP vulnerability causing reboots?
Hmmm, after more work I have it working.
1) Entered the IKE PSK into both dial-out and dial-in (the dial-in one was blank; the dial-out one had something showing)
2) Under Advanced, selected Aggressive mode and entered a string in Local ID (bizzarely this is the Dial OUT ID ???)
3) The Local ID string copied to Dial In / Peer ID
4) Disabled the Medium AH, DES, 3DES, leaving just AES
and, hey, it WORKS!
So we have the site-site VPN running like before but with this different config.
So I wonder what the PSK here does
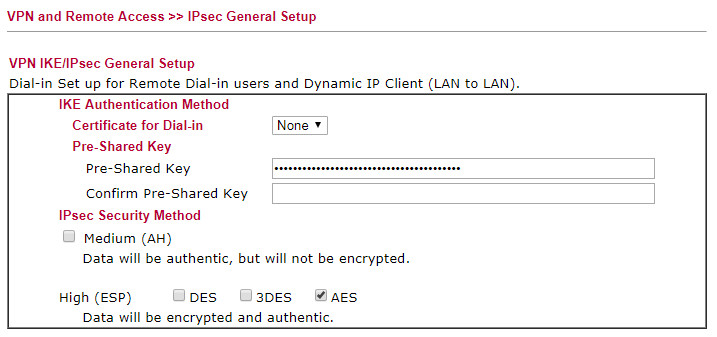
It says "Dial-in Set up for Remote Dial-in users and Dynamic IP Client (LAN to LAN)." So this is a 3RD place where the same PSK has to be configured...
Doubly weird since entering the PSK here
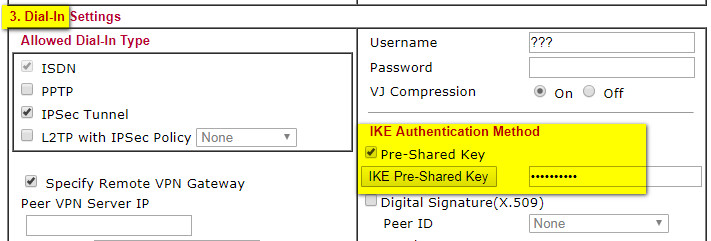
is what made it all work.
Android doesn't connect no matter what I do. There are actually very few options in android... This is the router screen
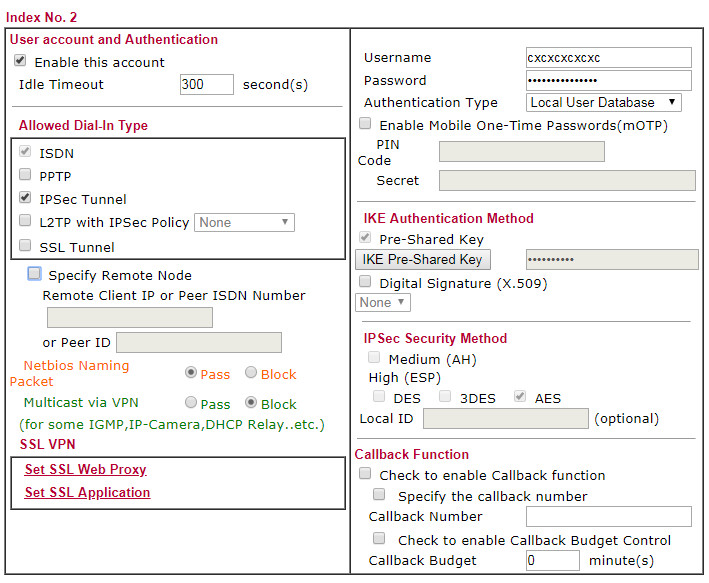
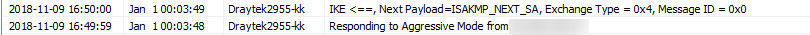
I have tried it with and without the Peer ID. Assuming Xauth is not supported, and assuming IKEV2 is, I have cleared out the Username and Password fields. In the phone there is just the "IPSEC Identifier" (= the Peer ID in the router) and the PSK. Doesn't connect though. Syslog shows nothing at all (shows plenty of stuff with the PPTP VPN which works). However if I change the android device fromIKEV2 to XAUTH, I see activity on syslog, but can't make out what it means. It just shows a load of identical messages
1) Entered the IKE PSK into both dial-out and dial-in (the dial-in one was blank; the dial-out one had something showing)
2) Under Advanced, selected Aggressive mode and entered a string in Local ID (bizzarely this is the Dial OUT ID ???)
3) The Local ID string copied to Dial In / Peer ID
4) Disabled the Medium AH, DES, 3DES, leaving just AES
and, hey, it WORKS!
So we have the site-site VPN running like before but with this different config.
So I wonder what the PSK here does

It says "Dial-in Set up for Remote Dial-in users and Dynamic IP Client (LAN to LAN)." So this is a 3RD place where the same PSK has to be configured...
Doubly weird since entering the PSK here

is what made it all work.
Android doesn't connect no matter what I do. There are actually very few options in android... This is the router screen

I have tried it with and without the Peer ID. Assuming Xauth is not supported, and assuming IKEV2 is, I have cleared out the Username and Password fields. In the phone there is just the "IPSEC Identifier" (= the Peer ID in the router) and the PSK. Doesn't connect though. Syslog shows nothing at all (shows plenty of stuff with the PPTP VPN which works). However if I change the android device fromIKEV2 to XAUTH, I see activity on syslog, but can't make out what it means. It just shows a load of identical messages

Please Log in or Create an account to join the conversation.
Moderators: Chris, Sami
Copyright © 2024 DrayTek


